Publications
Welcome to my research page!
I am deeply interested in exploring the intersection of Artificial Intelligence, Machine Learning, and Data Science, with a focus on developing scalable, practical solutions for real-world challenges. My research encompasses diverse domains, including Natural Language Processing (NLP), Cybersecurity, Churn Management, and Data Engineering in cloud ecosystems.
I have contributed to multiple peer-reviewed publications, combining theoretical analysis with practical experimentation to advance state-of-the-art techniques in my areas of interest.
Recent Research
1. Symbolic Regression for Aerosol–Cloud–Climate Interactions (in progress)
Graduate Researcher, Advisor: Duncan Watson-Parris Climate Analytics Lab, UC San Diego (2025 – Present)
Description:
Researching interpretable machine learning for climate science:
- Designed symbolic regression pipelines (PySR, SINDy, KAN) to extract physically meaningful mappings from satellite climate data.
- Benchmarked symbolic vs. deep neural networks (R² = 0.87 vs. 0.92).
- Built hybrid neural-to-symbolic architectures for explainability without performance loss.
- Deployed scalable HPC workflows on SDSC clusters for training, sensitivity analysis, and interpretability mapping.
2. BirdCLEF+ Acoustic Biodiversity Challenge (CLEF 2025, accepted)
CLEF 2025 Conference – First Author
Description:
Contributed to the BirdCLEF+ Kaggle competition by developing a scalable one-vs-rest detection pipeline for avian bioacoustics classification.
- Trained 206 per-species XGBoost models using log-mel spectrograms and geo-contextual metadata.
- Engineered 3,200-dimensional sparse features via adaptive STFT-based binning with class balancing.
- Improved low-resource species performance (F1 ↑ from 0.00 → 0.72).
- Achieved >0.90 mean AUC across species.
Selected Publications
1. Toxic Tweet Classification on Twitter
S. S. Gokulnath, S. Jayaraman and N. T, “A Comprehensive Examination of Toxic Tweet Classification on Twitter,” 2024 Ninth International Conference on Science Technology Engineering and Mathematics (ICONSTEM), Chennai, India, 2024, pp. 1-5, doi: 10.1109/ICONSTEM60960.2024.10568694
Description:
This study explores advanced NLP techniques to detect and classify toxic tweets on Twitter. We evaluated both traditional machine learning models and transformer-based architectures for identifying toxicity levels in user-generated content. Our experiments highlighted the robustness of transformers like BERT in handling the nuances of toxic language.
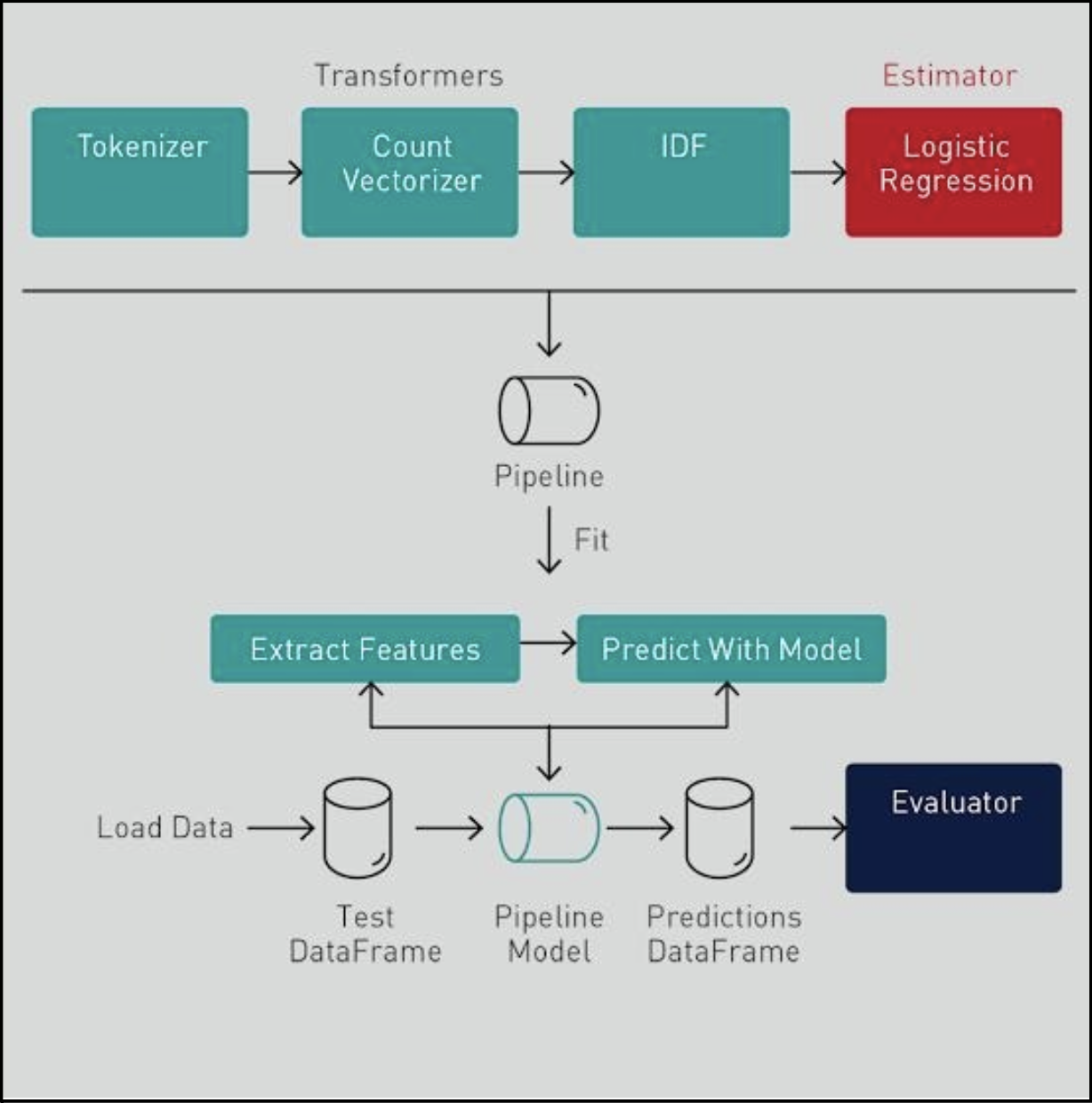
Figure 1: Transformer-based Toxic Tweet Classification Architecture
2. Churn Management Using Azure Ecosystems
S. S. Gokulnath and M. Revathi, “Leveraging Data Analytics in Azure for Effective Churn Management,” 2024 Second International Conference on Emerging Trends in Information Technology and Engineering (ICETITE), Vellore, India, 2024, pp. 1-10, doi: 10.1109/ic-ETITE58242.2024.10493670.
Description:
This research focuses on leveraging Azure Data Factory, Synapse Analytics, and Event Hubs for building an end-to-end churn management system. The study demonstrates how data pipelines and machine learning models were used to predict churn probability, achieving significant improvements in churn detection accuracy.
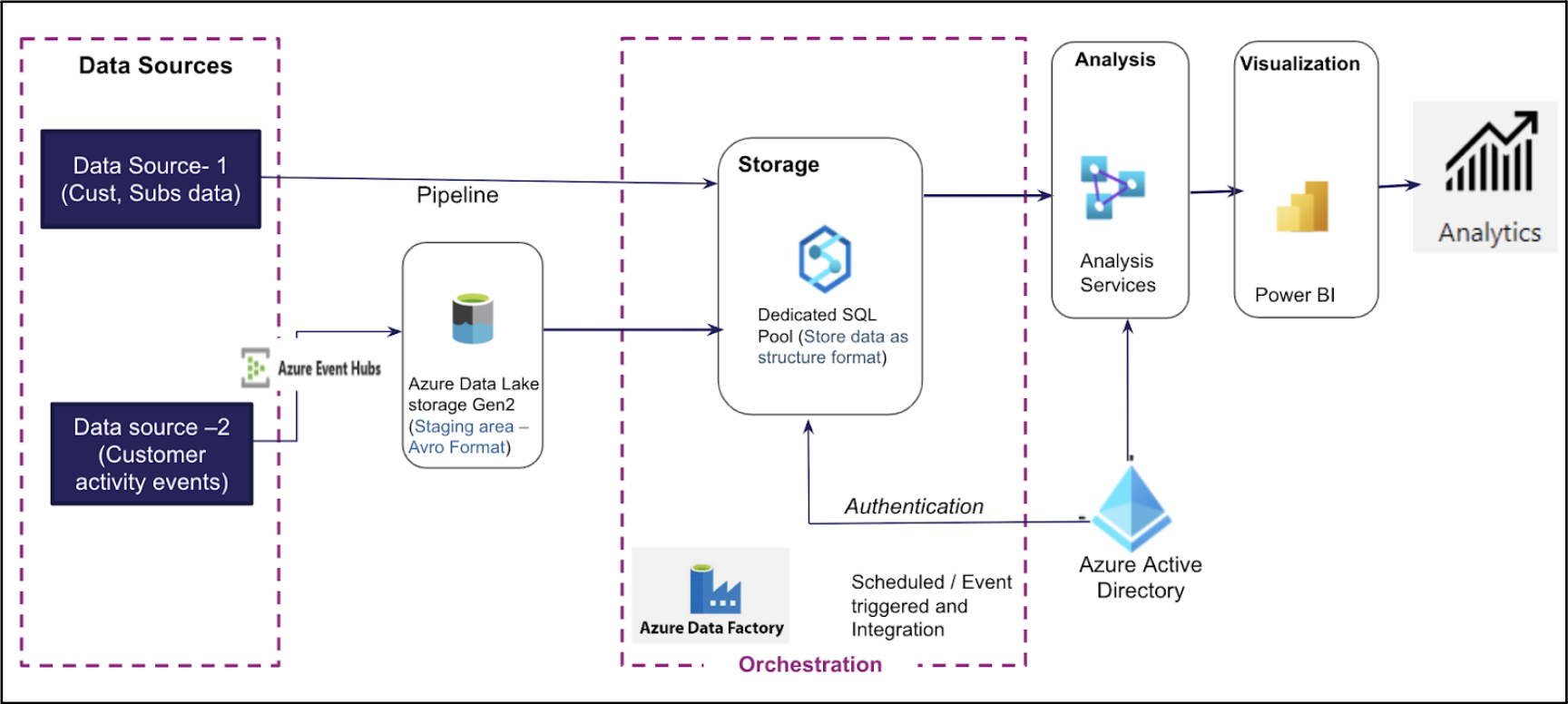
Figure 2: Azure Ecosystem for Churn Management
3. Comparative Analysis of NLP Architectures
T. Subbulakshmi, P. L. Narayan, S. S. Gokulnath, R. Suganya and G. H. Subramanian, “Analysis of Traditional and Deep Learning Architectures in NLP: Towards Optimal Solutions,” 2023 6th International Conference on Recent Trends in Advance Computing (ICRTAC), Chennai, India, 2023, pp. 760-765, doi: 10.1109/ICRTAC59277.2023.10480825.
Description:
In this study, we conducted a comparative evaluation of traditional machine learning models versus deep learning approaches for NLP tasks like sentiment analysis and named entity recognition. LSTM and GRU models demonstrated superior performance due to their ability to capture sequential dependencies in text.
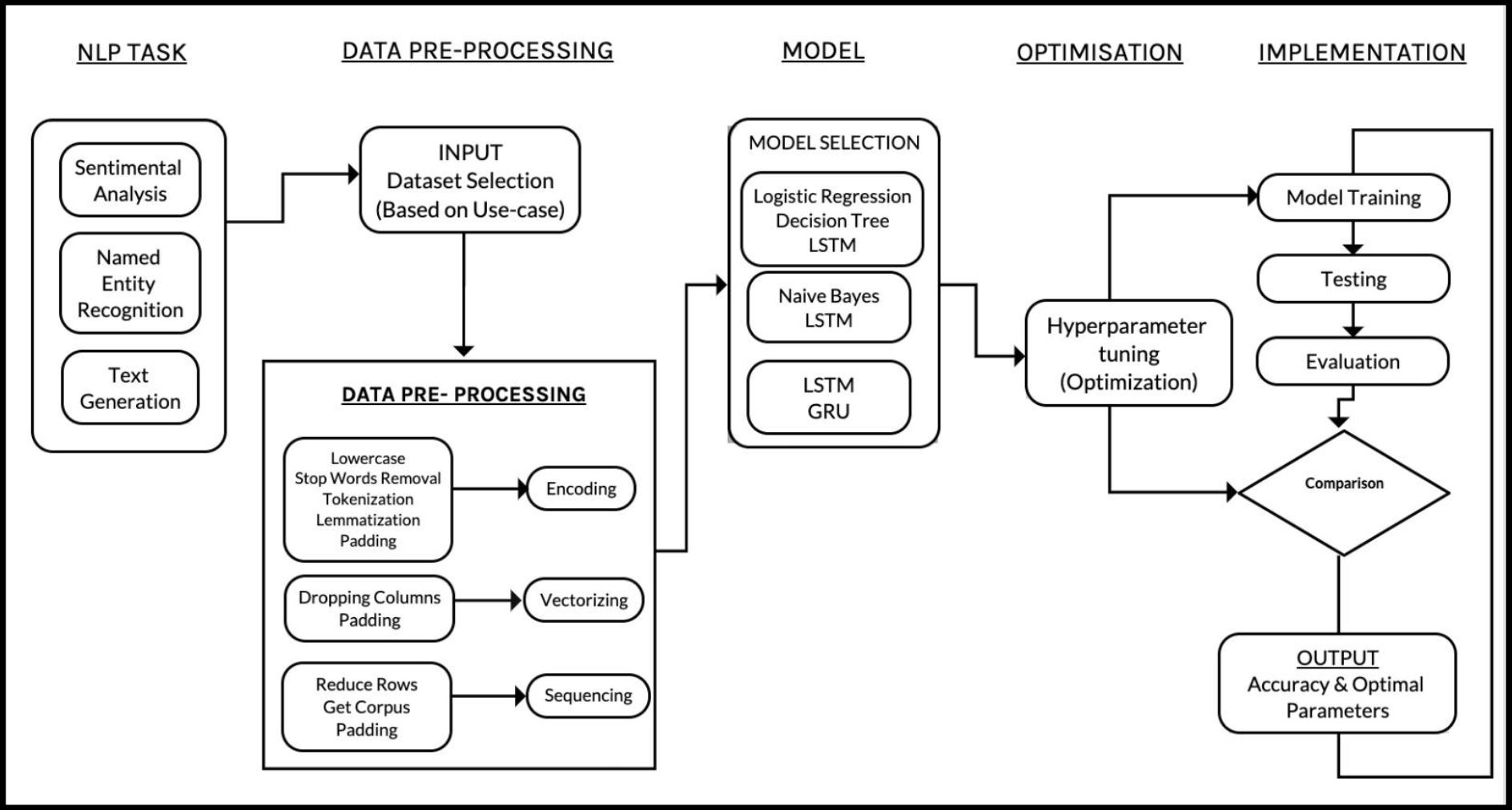
Figure 3: Deep Learning Architectures for NLP Tasks
4. Evolution of DDoS Detection Models
V. Premanand, S. S. Gokulnath, S. Jayaraman and S. Bhaskar, “Analyzing the Evolution of DDoS Attack Detection: Traditional vs. Modern Machine Learning Models,” 2023 6th International Conference on Recent Trends in Advance Computing (ICRTAC), Chennai, India, 2023, pp. 772-777, doi: 10.1109/ICRTAC59277.2023.10480859.
Description:
This research examines the evolution of DDoS attack detection techniques, comparing traditional rule-based approaches to machine learning models. We highlight the advantages of modern deep learning models, particularly in detecting patterns in large-scale network traffic data.
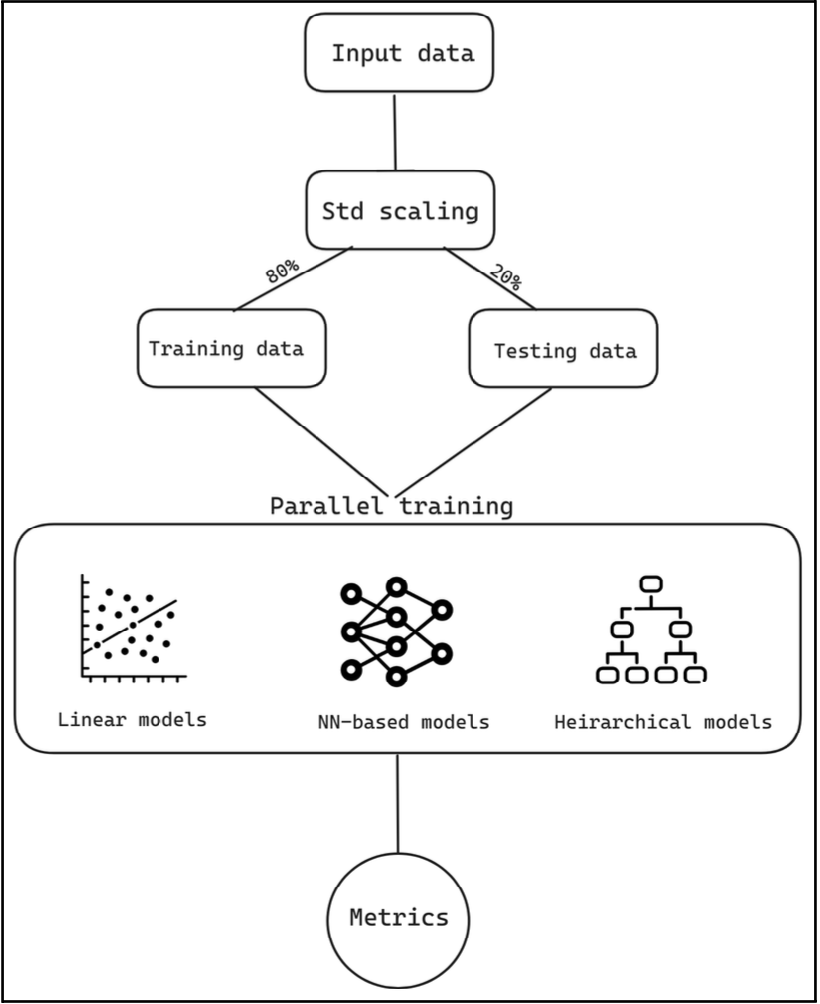
Figure 4: AI-Powered DDoS Detection Pipeline
